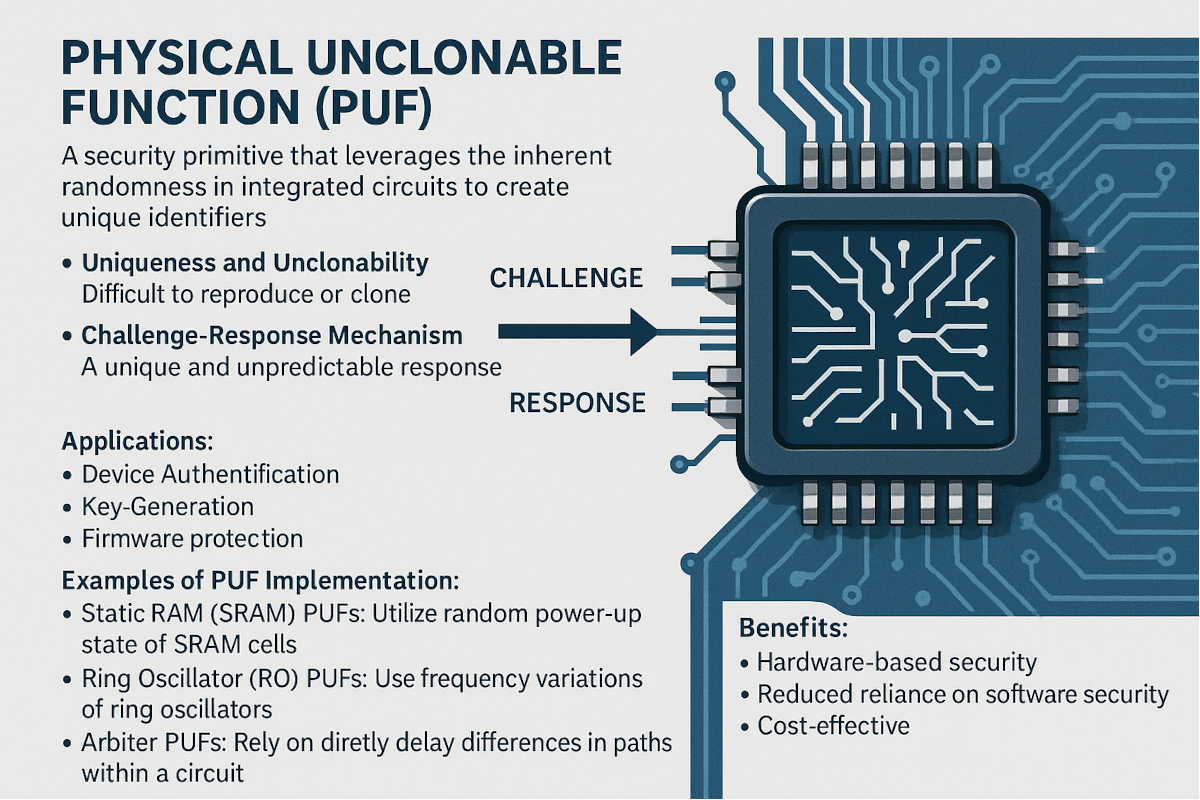
A Physical Unclonable Function (PUF) is a security primitive, primarily used in hardware security, that leverages the inherent physical randomness in integrated circuits to create unique identifiers. Think of it as a digital fingerprint for a specific device, generated using the unpredictable intrinsic manufacturing variations.
Here’s a more detailed explanation:
- Uniqueness and Unclonability:PUFs are designed to be unique to a specific chip or device, making them difficult to reproduce or clone. This uniqueness stems from the random variations that occur during the manufacturing process of integrated circuits.
- Challenge-Response Mechanism:PUFs operate based on a challenge-response mechanism. When a challenge (an input) is presented to the PUF, it produces a unique and unpredictable response (an output). This response acts as a fingerprint for the device.
- Applications:PUFs are used for various security applications, including:
- Device Authentication: Verifying the identity of a device.
- Key Generation: Creating unique cryptographic keys for encryption and secure communication.
- Anti-counterfeiting: Protecting against the counterfeiting of electronic devices and products.
- Firmware Protection: Binding software to specific hardware, preventing unauthorized software from running.
- Examples of PUF Implementation:
- Static RAM (SRAM) PUFs: Utilize the random power-up state of SRAM cells.
- Ring Oscillator (RO) PUFs: Use the frequency variations of ring oscillators.
- Arbiter PUFs: Rely on the delay differences in paths within a circuit.
- Benefits:
- Hardware-based security: Provides a hardware-level security mechanism that is difficult to bypass.
- Reduced reliance on software security: Minimizes the need for complex software-based security measures.
- Cost-effective: Can be implemented relatively easily and cost-effectively.
